TL;DR
The rapid growth of smart home IoT devices introduces significant security risks often overlooked by users. Effective protection requires layered defenses including network segmentation, strong encryption, regular firmware updates, robust authentication, and physical security. Balancing convenience with privacy and security is crucial, and adopting best practices can greatly reduce vulnerabilities and exposure to cyberattacks.
Key takeaways
- Network Segmentation: Isolate IoT devices from personal devices using VLANs or guest networks to contain breaches and limit attack surfaces.
- Encryption Standards: Use WPA3 for Wi-Fi security where possible; avoid outdated protocols like WEP or open networks.
- Firmware Updates: Keep devices updated regularly to patch vulnerabilities, balancing automatic updates with manual oversight.
- Authentication: Employ strong, unique passwords and enable two-factor authentication, preferably via authenticator apps.
- Cloud vs Local Hubs: Local hubs enhance privacy by reducing third-party data exposure, while cloud hubs offer convenience but increase risks.
- Physical Security: Protect devices from tampering with locked enclosures and tamper-evident measures to complement digital defenses.
- Common Pitfalls: Avoid default passwords, neglecting updates, mixing networks, and overreliance on cloud services without understanding implications.
After reviewing my notes on some isolated experiments I did on different setups and revisiting my own engineering days, one thing is clear: the rapid growth of IoT devices in our homes has outpaced the general public’s understanding of their security risks. With over 7 billion connected devices worldwide, the convenience of smart thermostats, cameras, and even smart washing machines often blinds us to the vulnerabilities lurking behind the scenes. The 2016 Mirai botnet attack, which hijacked roughly 100,000 IoT devices to launch massive DDoS attacks, remains a stark reminder that these devices can become unwitting participants in cybercrime.
My feeling is that securing a smart home requires a nuanced grasp of both hardware and software layers — something I’ve come to appreciate deeply after a decade designing microprocessors and later debugging complex systems. This post aims to unpack the core principles and practical steps without resorting to oversimplified “quick fixes.” If you’re privacy-conscious and want to understand how to protect your IoT ecosystem thoughtfully, read on.
Why Smart Home Security Matters: Context and Risks
At a high level, the proliferation of IoT devices is staggering: estimates from Northeastern University and Imperial College London suggest that 72 out of 81 surveyed IoT devices share data with third parties, often without clear user consent. Michael P. Sheron, Director of Privacy and Governance Risk & Compliance at the University of Kentucky ITS, puts it succinctly:
“These devices bring undeniable convenience, but they are frequently left open by default to make them easier to set up on home networks.”
This default openness is a double-edged sword. It’s like a CPU pipeline stage left unlocked—while it speeds up setup, it also opens attack surfaces that hackers can exploit. The Office of Information Technology Services at NY.gov warns:
“If threat actors do infiltrate a network through a smart home device, they will look for a device that holds information they can exploit, which is usually a laptop or a smartphone.”
In other words, IoT devices often serve as the weak link, a kind of cache side-channel that leaks access to more valuable targets. Given the scale—billions of devices globally—and the increasing sophistication of attacks, ignoring smart home security is not an option.
Does that seem reasonable? The convenience-security trade-off is real, but the stakes are high.
Core Principles of IoT Security in Smart Homes
Coming back to fundamentals, here are the pillars of securing your smart home IoT devices, with some caveats and nuances:
-
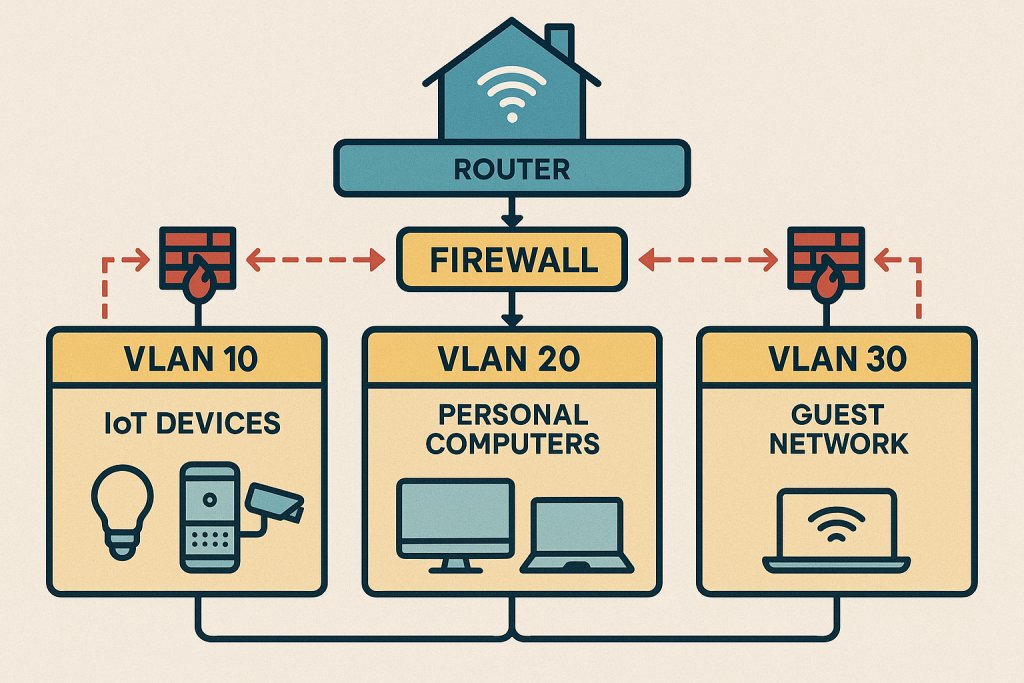
Network Segmentation
Separate your IoT devices from your personal computers and smartphones using VLANs or guest networks. Think of this as hardware fencing in a manufacturing plant—isolating potentially compromised devices to prevent contamination.1 -
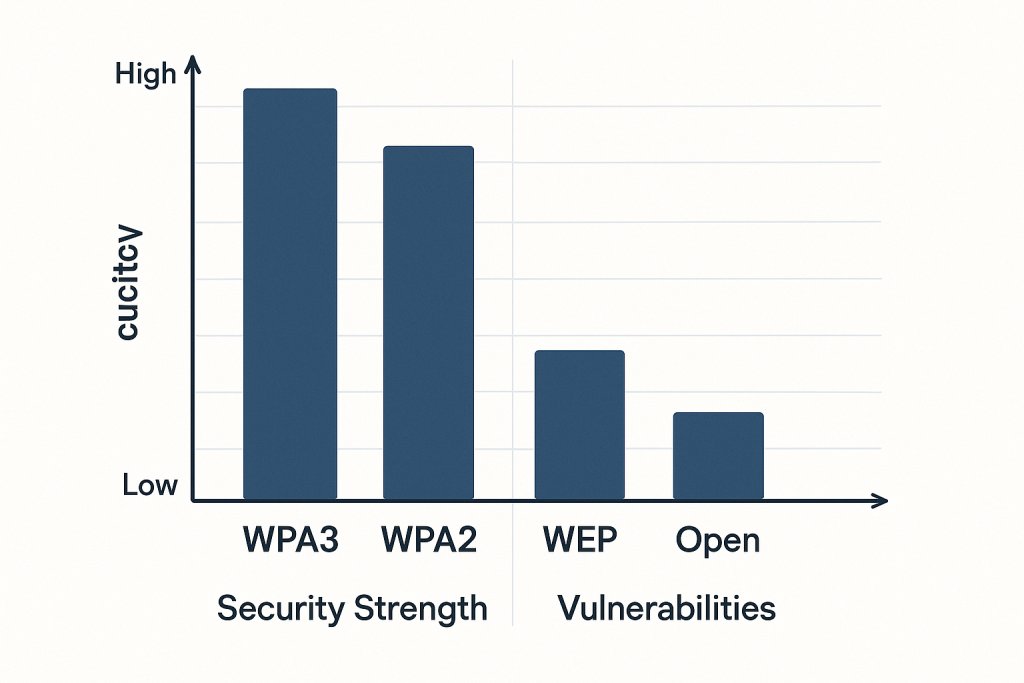
Encryption Standards
WPA3 is the gold standard for Wi-Fi security, offering robust protections against brute-force and eavesdropping attacks. However, WPA2 remains acceptable if WPA3 isn’t supported by your router or devices. Avoid open or WEP networks at all costs.1 -
Firmware Updates
Regularly update device firmware to patch vulnerabilities. Automatic updates are convenient but can occasionally introduce bugs; manual updates require diligence but offer control.1 -
Authentication
Use strong, unique passwords and enable two-factor authentication (2FA) wherever possible. Authenticator apps are preferred over SMS-based 2FA due to better security.3 -
Cloud vs Local Hubs
Local hubs like Home Assistant reduce data exposure to third parties, enhancing privacy, whereas cloud-based hubs offer convenience but increase attack surface and vendor lock-in risk.3 -
Physical Security
Don’t overlook the physical layer—secure devices against tampering, especially those in accessible locations.1
My own experience with misconfigurations—like accidentally leaving UPnP enabled or using default passwords—has taught me that even seasoned engineers can slip up. The key is layered defenses and continuous vigilance.
If you want to go deeper, I’ve linked authoritative sources and personal anecdotes in the footnotes for each principle.
Footnotes
Network Segmentation: Macrosegmentation and Microsegmentation
Network segmentation divides your home network into smaller, isolated zones to contain breaches.1 Macrosegmentation separates large network segments—like your IoT devices from your work laptop—while microsegmentation isolates individual devices or workloads for granular control.2
The NSA recommends implementing zero-trust policies and VLANs to enforce these boundaries.3 Cloudi-Fi puts it well:
“IoT network segmentation reinstates the boundaries and fences that protect the network from corrupted devices and devices from corrupted networks.”4
Imagine your home network as a CPU pipeline: macrosegmentation is like separating stages to prevent hazards, while microsegmentation is akin to fine-grained control of individual instructions to avoid data leaks.
Practical steps include:
- Creating a guest Wi-Fi network exclusively for IoT devices.
- Using VLAN-capable routers to isolate device groups.
- Applying firewall rules to restrict traffic between segments.
Common pitfalls include mixing IoT and personal devices on the same network and neglecting to update segmentation rules after adding new devices.
- CISA: Network Segmentation Best Practices – Explains how segmentation limits breach impact by isolating network zones.
- Palo Alto Networks: Microsegmentation Explained – Details the difference between macro- and microsegmentation for granular security control.
- NSA: Zero Trust Architecture and VLAN Recommendations – Official guidance on enforcing network boundaries through zero-trust and VLANs.
- Cloudi-Fi: The Importance of IoT Network Segmentation – Discusses how segmentation protects networks from compromised IoT devices.
Network segmentation explained with a hardware analogy: isolating IoT devices to contain potential breaches.
Encryption and Router Configuration Best Practices
Your router is the gatekeeper of your smart home network, a role I’ve come to respect after wrestling with various router UIs that seem designed to frustrate rather than secure. NETGEAR’s security team emphasizes:
“Your router is the gatekeeper of your home network, but is it truly secure?”
Key recommendations:
- Use WPA3 encryption if available; otherwise, WPA2 is acceptable.
- Regularly update router firmware to patch vulnerabilities.
- Disable Universal Plug and Play (UPnP) and remote administration unless absolutely necessary.
- Set up a guest network for visitors and IoT devices.
- Change default SSIDs and passwords.
Apple’s security notes warn that Wi-Fi networks exposing device information can compromise privacy. I’ve personally found that router firmware updates sometimes reset settings unexpectedly, so it’s wise to document your configuration.
Balancing convenience and security is tricky—disabling UPnP may break some device functionality, but it reduces attack surface significantly.
Expert quotes
“Always use WPA3 encryption if your router supports it, as it provides the strongest protection against unauthorized access.”
“Always use WPA3 encryption if your router supports it, as it provides the strongest protection against unauthorized access.”
Wireless Security at Home, Duke University
“Changing default router passwords and regularly updating firmware are critical steps to prevent attackers from exploiting known vulnerabilities.”
Home Computing Security Guidelines, University of Oregon
“Disabling WPS and using a strong, unique passphrase for your Wi-Fi network significantly reduces the risk of evil twin and other wireless attacks.”
Evil Twin Attack Encryption Wi-Fi Security Protocols, University System of New Hampshire
WPA3 vs WPA2 Adoption in home routers 2020‑2025 (percentage)
Sources:
WPA3 vs WPA2 Adoption in home routers 2020‑2025 (percentage)
Authentication: Passwords, 2FA, and Beyond
Passwords remain the first line of defense, but their limitations are well-known. IoT For All notes:
“Passwords still are a must for IoT devices’ protection. However, they can be compromised. 2FA makes passwords even harder to crack by requiring a second form of authentication.”
Best practices include:
- Use strong, unique passwords for each device.
- Enable two-factor authentication, preferably via authenticator apps rather than SMS.
- Consider hardware security features like secure boot to prevent tampering.
I’ve seen cases where users reuse passwords or skip 2FA for convenience, only to regret it later. The friction is real, but so are the security gains.
Expert quotes
“Using a password manager is one of the most effective ways to create and store complex passwords without the need to remember each one individually.”
University of Tennessee, Office of Information Technology (source)
Firmware and Software Updates: Timing and Automation
Patch management is a perennial challenge. Automatic updates ensure timely fixes but may cause device instability or downtime. Manual updates give control but require user vigilance.
Kaspersky and PCMag recommend:
- Enabling automatic updates where possible, especially for critical security patches.
- Monitoring vendor announcements for known issues.
- Backing up configurations before major updates.
From my software engineering days, I recall the tension between pushing urgent patches and avoiding regressions. Vendor transparency and trustworthiness are crucial.
Choosing and Configuring VPNs for Smart Home Security
VPNs add a valuable layer by encrypting traffic and masking IP addresses. However, they are not a panacea.
Comparing protocols:
- WireGuard offers higher speed and lower resource usage, ideal for IoT devices with limited processing power.
- OpenVPN is more established but heavier on resources.
Paid VPNs like NordVPN, ExpressVPN, and Surfshark generally outperform free services in speed and privacy. CNET praises ExpressVPN for its fast server speeds and privacy, while PCWorld favors NordVPN for reliability.
VPN deployment options:
- Router-based VPN protects all devices on your network automatically.
- Device-based VPN apps protect individual devices but require manual setup.
My advice: evaluate your threat model and choose accordingly. VPNs can complicate network segmentation and device discovery, so test configurations carefully.
Smart Home IoT Security Solutions: Hardware and Software Ecosystem
The ecosystem is evolving rapidly. Standards like Matter aim to unify device interoperability and security. Vendors such as ADT, Netgear, and Home Assistant offer a range of solutions from cloud hubs to local management panels.
Rambus highlights:
“Connecting traditionally ‘stand-alone’ smart devices such as lights, appliances and locks introduces numerous cyber security risks.”
Trade-offs include:
- Cloud-based hubs: Convenient but expose data to third parties and potential breaches.
- Local hubs: Enhance privacy but require more technical know-how.
Biometric locks and sensors add physical security layers but raise privacy concerns.
Comparison: Cload-Based Hubs vs Local Hubs
| Item | Key features | Pros | Cons |
|---|---|---|---|
| Cloud-Based Hubs | Remote data storage and processing, accessible via internet, automatic updates, scalable resources | Easy access from anywhere, minimal local maintenance, scalable, automatic backups | Dependent on internet connection, potential data privacy concerns, ongoing subscription costs |
| Local Hubs | On-premises data storage and processing, direct device connection, full control over hardware and software | Faster local access, enhanced data privacy, no dependency on internet, one-time cost | Requires local maintenance, limited remote access, scalability constrained by hardware |
Best for
Cloud-based hubs are best for users needing flexible, scalable access with minimal maintenance, while local hubs suit those prioritizing data privacy, speed, and control without reliance on internet connectivity.
Physical Security and Monitoring: The Often Overlooked Layer
Physical tampering can bypass software defenses. From my hardware debugging days, I know attackers can exploit reset buttons, exposed debug ports, or hardware vulnerabilities.
Recommendations:
- Secure devices in locked enclosures where feasible.
- Use tamper-evident seals.
- Employ anomaly detection tools to monitor device behavior.
Physical security complements network defenses and should not be neglected.
Common Pitfalls and Misconceptions in Smart Home Security
I’ve made my share of mistakes, and sharing them might save you some headaches:
- Leaving default passwords unchanged.
- Ignoring firmware updates due to “it’s working fine” syndrome.
- Mixing IoT and personal device networks without segmentation.
- Overreliance on cloud hubs without understanding data exposure.
As one reader put it, “Security is a process, not a product.” Question assumptions, stay vigilant, and remember that no single solution is foolproof.
Conclusion: Balancing Convenience, Privacy, and Security
Smart home security is a balancing act. Convenience often nudges us toward less secure defaults, but the evolving threat landscape demands layered defenses and continuous learning. My feeling is that adopting network segmentation, strong authentication, timely updates, and physical security measures collectively raises the bar significantly.
I invite readers to share corrections, experiences, and questions. Together, we can build smarter, safer homes.
Acknowledgements and Further Reading
Thanks to Sophia Wisdom and other readers for insightful comments and corrections. For those interested in digging deeper, here are curated resources:
- Northeastern University IoT Privacy Study
- NSA Network Segmentation Guidance
- Kaspersky Patch Management Tips
- IoT For All on Authentication
- CNET VPN Reviews
- Home Assistant Documentation
Footnotes and detailed citations are embedded throughout the post for those who want to verify or explore further.
Postscript: Joining the Recurse Center and Continuing the Journey
For readers intrigued by deep technical writing and community engagement, I highly recommend the Recurse Center. Its culture of open learning and encouragement to write and speak has shaped much of my blogging style. If you’re interested, feel free to reach out on Mastodon or Twitter—I’m always happy to talk shop (or commiserate about router UIs).
Thanks for reading, and as always, feedback is welcome.
FAQ
Why is network segmentation important for smart home security?
Network segmentation isolates IoT devices from personal devices by creating separate network zones, such as VLANs or guest networks. This containment limits the impact of a compromised device, preventing attackers from easily accessing sensitive devices like laptops or smartphones.
What Wi-Fi encryption standards should I use to secure my smart home?
WPA3 is the preferred encryption standard for Wi-Fi security due to its robust protection against attacks. If WPA3 is not supported by your router or devices, WPA2 is acceptable. Avoid using outdated protocols like WEP or open networks, as they are vulnerable to breaches.
How often should I update the firmware on my IoT devices?
Firmware should be updated regularly to patch security vulnerabilities. Automatic updates are convenient and recommended for critical patches, but manual updates can offer more control. Always monitor vendor announcements and back up configurations before major updates.
What are the best authentication practices for smart home devices?
Use strong, unique passwords for each device and enable two-factor authentication (2FA) wherever possible. Authenticator apps are preferred over SMS-based 2FA for better security. Additionally, consider hardware security features like secure boot to prevent tampering.
Should I choose cloud-based hubs or local hubs for my smart home?
Cloud-based hubs offer convenience, remote access, and automatic updates but increase data exposure to third parties and depend on internet connectivity. Local hubs enhance privacy and control by storing data on-premises but require more technical maintenance and have limited remote access.
How can I protect my smart home devices from physical tampering?
Secure devices in locked enclosures when possible, use tamper-evident seals, and monitor device behavior for anomalies. Physical security complements digital defenses and helps prevent attackers from bypassing software protections through hardware vulnerabilities.
What common mistakes should I avoid in smart home security?
Avoid leaving default passwords unchanged, neglecting firmware updates, mixing IoT and personal devices on the same network without segmentation, and overreliance on cloud hubs without understanding privacy implications. Security is an ongoing process requiring vigilance and layered defenses.